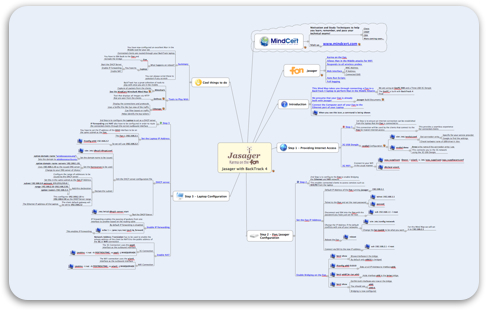
After seeing some guys at Shmoocon 2010 with a neat Jasager BackTrack setup I thought I would go about creating a Mind Map on how to set this up.
So, I sat down with Robin Wood aka DigiNinja, the creator of Jasager for the day to go through how to set this up.
If you are new to Jasager be sure to read the original project pages to see what it can do.
Also, check out a recent Hak5 episode that shows Darren from Hak5 doing the Airport WiFi challenge.
This Mind Map takes you through how to create a cool Man in the Middle WiFi solution using a default install of both Jasager and BackTrack 4.
The Jasager responds to all WiFi probe requests and then the BackTrack 4 device allocates an IP address from its DHCP server and enables onwards routing to the Internet via a 3G modem or WiFi connection.
I built my solution using a Fon+ and an EeePC 900 running BackTrack 4. I have used both my 3G card and also my MiFi to provide onwards Internet. The solution works great and I have been able to do some fantastic demonstrations with this set up.
Click Here to Download the Mind Map and please let me now if you have any comments, good or bad.