 Here is the fifth Mind Map in the Certified Ethical Hacker CEH series from MindCert.com.
Here is the fifth Mind Map in the Certified Ethical Hacker CEH series from MindCert.com.
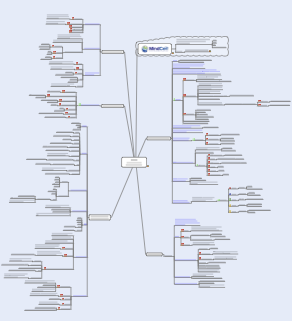
This Mind Map covers System Hacking. There are nine sections to this Mind Map.
They are: Remote Password Guessing, Eavesdropping, Denial of Service, Privilege Escalation, Keystroke Loggers, Password Cracking, Covering Tracks, Remote Control, and Covering Tracks.
This is quite a large Mind Map as you can see and it covers a lot of topics. As normal, the subjects are covered and then associated tools are provided complete with links that show where to download the tools from. All of the tools are what are in the CEH syllabus and I would recomend you looking at each one of these tools in order to ensure you know what they do, and how they do it.
The CEH exam has a large focus on the tools you use so take advantage of these links and install the tools to play with. You cannot beat first hand experience.
As always, please feed back comments about the Mind Map and follow this link to download it.